The National Institute of Standards and Technology (NIST) on Thursday released an updated cybersecurity guidance for managing risks in the supply chain, as it increasingly emerges as a lucrative attack vector.
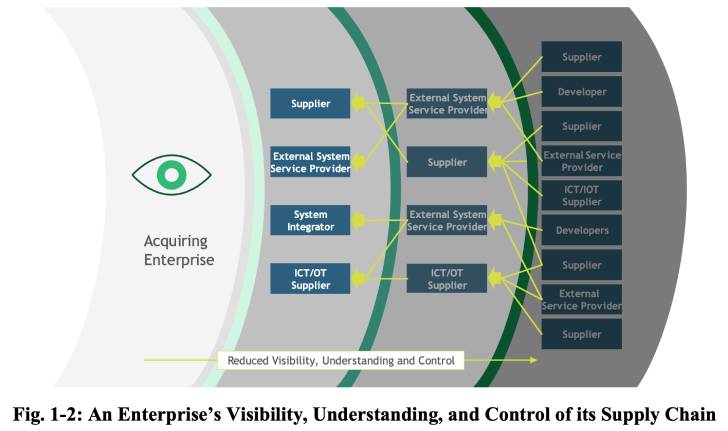
“It encourages organizations to consider the vulnerabilities not only of a finished product they are considering using, but also of its components — which may have been developed elsewhere — and the journey those components took to reach their destination,” NIST said in a statement.\
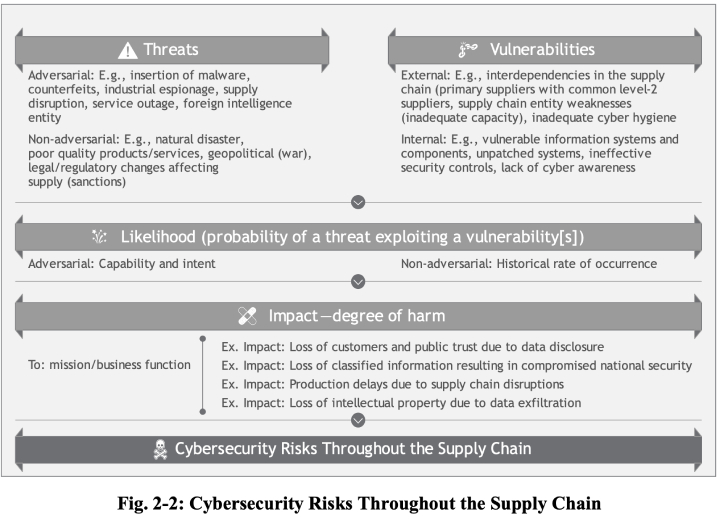
The new directive outlines major security controls and practices that entities should adopt to identify, assess, and respond to risks at different stages of the supply chain, including the possibility of malicious functionality, flaws in third-party software, insertion of counterfeit hardware, and poor manufacturing and development practices.
The development follows an Executive Order issued by the U.S. President on “Improving the Nation’s Cybersecurity (14028)” last May, requiring government agencies to take steps to “improve the security and integrity of the software supply chain, with a priority on addressing critical software.”
It also comes as cybersecurity risks in the supply chain have come to the forefront in recent years, in part compounded by a wave of attacks targeting widely-used software to breach dozens of downstream vendors all at once.